How It Works
The Behavioral Orchestration Layer: Transform behavior from manual coding into modular, configurable scenarios
The Workflow
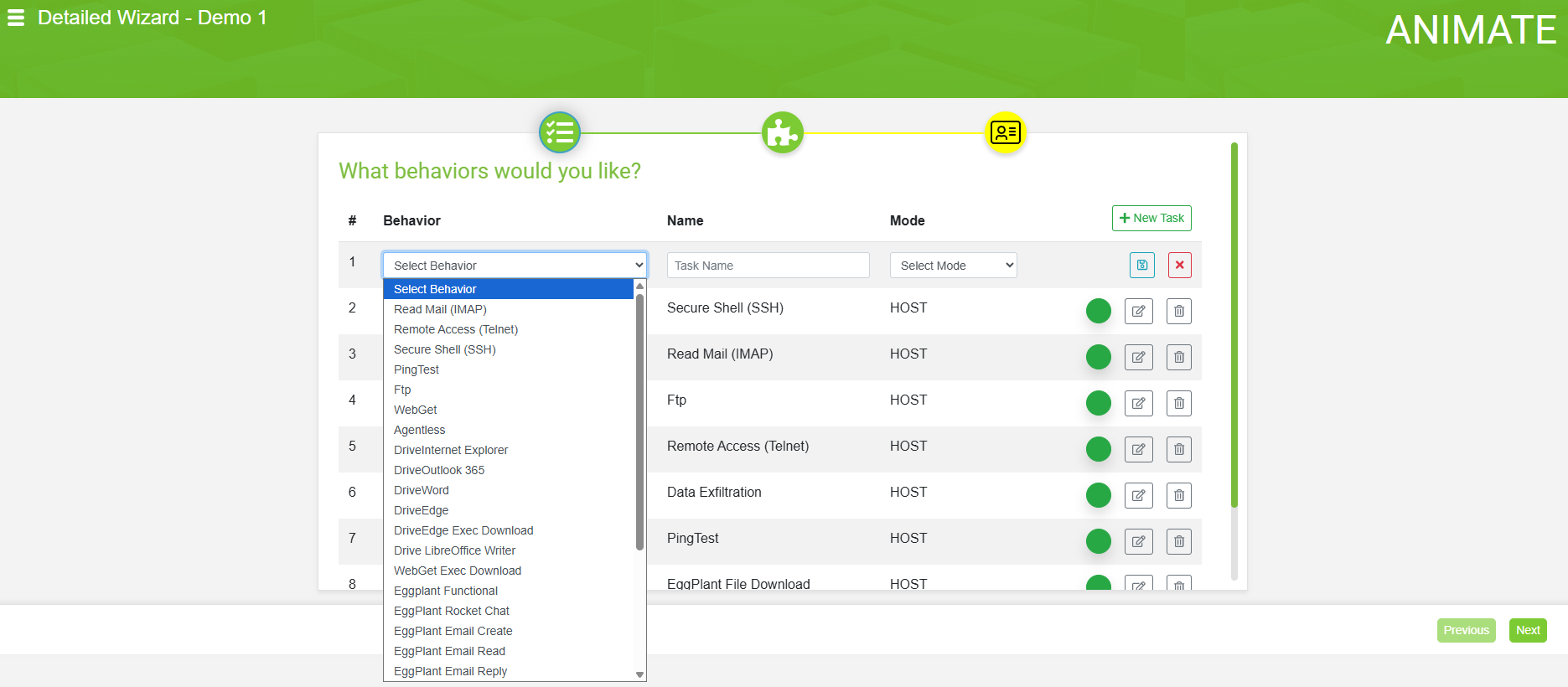
Configure
Define desired outcomes and roles without scripting. Select behaviors from library, map to environment.
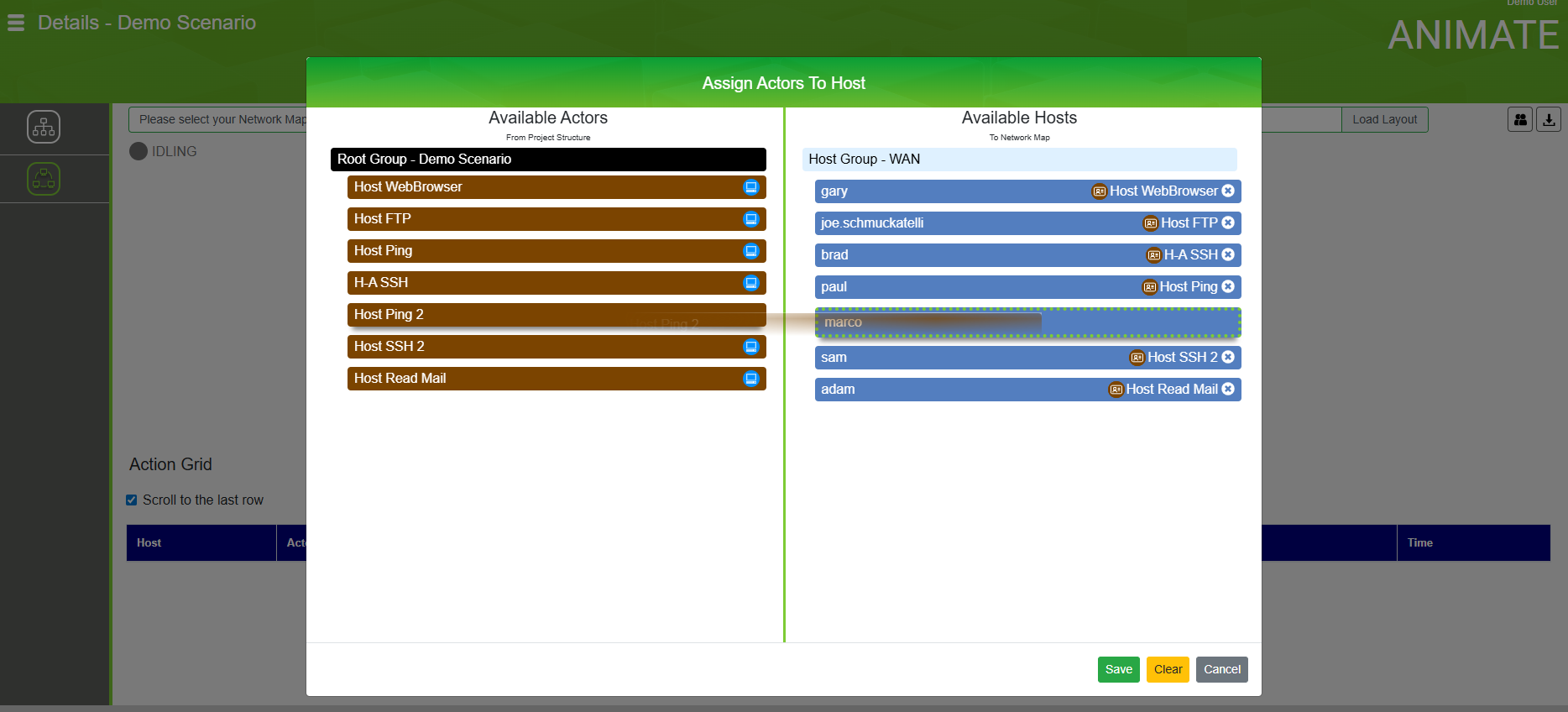
Deploy
Bind reusable behaviors to existing topologies and tools via network trunking. Zero host software.
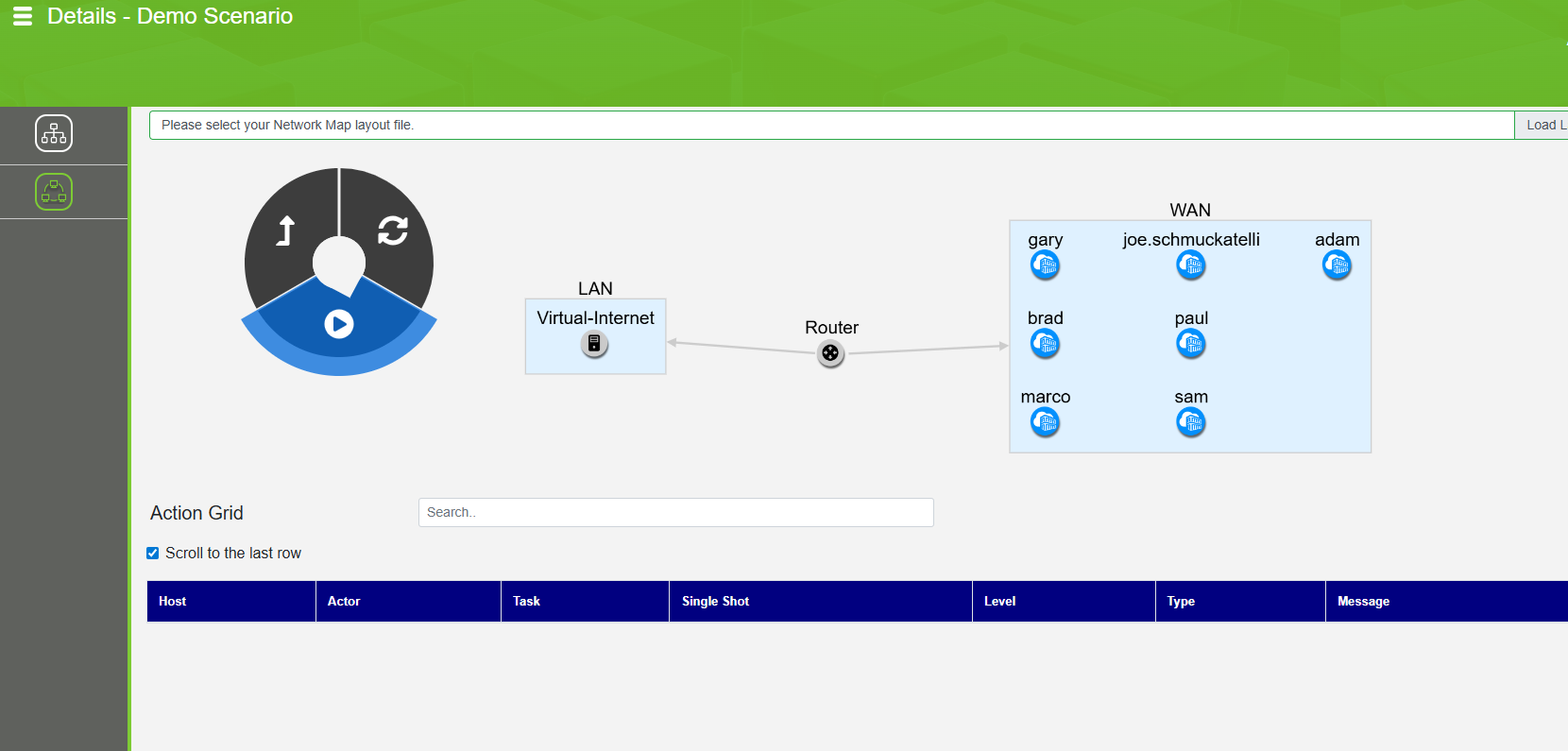
Execute
Behavior executes with defined placement, timing, and constraints. Each run produces unique patterns.
📊 Scenario Studio Interface
Visual configuration interface for building scenarios without code
⚙️ BDK Workflow
Python-based Behavior Development Kit for creating reusable assets
Traditional vs. Animate
❌ Traditional Scripting
- ⏱️ Weeks to build one scenario
- 📋 Manual coding for every change
- 📄 Constant re-imaging after exercises
- 📉 Zero reusability across environments
- 🎯 Static, predictable patterns
✅ Animate Configuration
- ⚡ Hours to build and deploy
- 🎨 GUI-based configuration
- ✨ Pristine infrastructure, no cleanup
- ♻️ Fully reusable across topologies
- 🎲 Stochastic, realistic patterns
🎯 Centralized Project Operations
Define, place, and evolve behavior without rebuilding the environment. Modify through configuration, not environment rebuilds.
⚡ Intent-Driven Execution
Behavior originates from the correct level of effect (network, host, or device). Execution follows defined placement, timing, and constraints.
📄 Reusable Scenarios
Reuse scenarios without destabilizing the environment. Behaviors are decoupled from infrastructure.
📊 Unique Patterns
Each run produces unique patterns of life signals within defined bounds. Artifacts emerge naturally from execution.
Proven Scale: Successfully orchestrated 50-100 users. Theoretically unlimited scalability through hierarchical attribution—update one global attribute to cascade changes instantly across all actors.


